DeadFace CTF 2021 Writeups
Hey guys!! This weekend I participated in the DeadFace CTF 2021 which was based on a stimulated story of a Hacker Group called DeadFace. I enjoyed a lot while playing this CTF. I participated solo in this CTF and I scored a total of 1550 which placed me at 277th place on the leaderboard. Hope you’ll have fun reading my writeups.
OSINT
Occupation
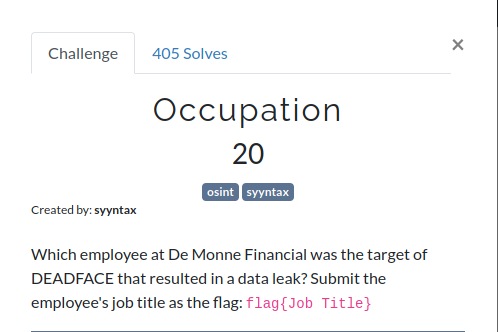
In this challenge, we are given the above image which says that who was the person which was responsible for the data leak in the De Monne Financial. So, firstly, I looked up at the forum of the DEADFACE hacker group and there was a post in there which talks about a person who was arrested for the data leak.
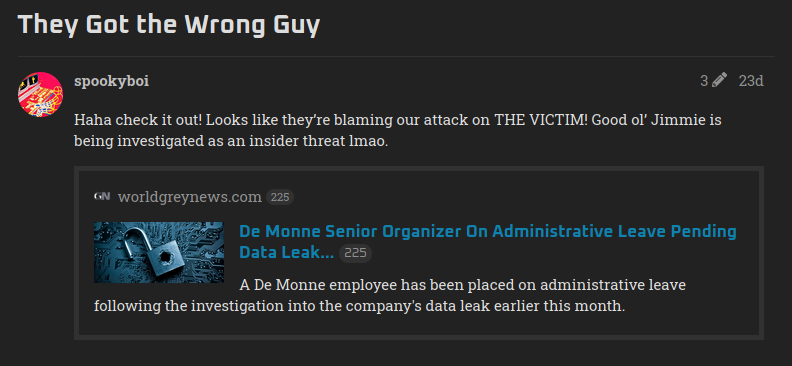
So when we open the above article, we get the name of the person who was responsible for the data leak at De Monne Financial. The person name is Jimmie Castora but we have to find the job title of this person so the next thing I did is searched this person on Google and luckily I landed on his linkedin profile.
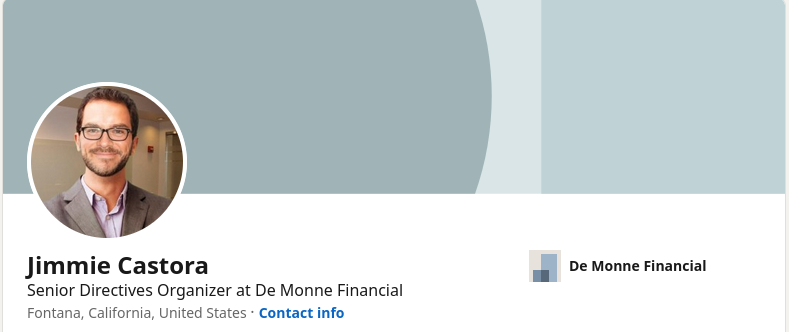
And we got the profile job of the person. Therefore, the flag for this CTF is:
flag{Senior Directives Organizer}
Meetup
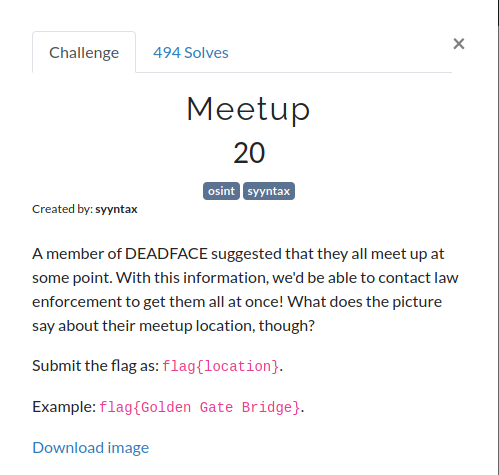
In this challenge, we are given the below image of a chair and we’ll have to find the location of this chair. So, let’s fired up the Google Reverse Image Search. GooooooooooooooOOOOOOO!!

After searching for this image, I came up with the name of Eastern State Penitentiary and according to the wikipedia, the image in the above chair was used by a barber in the Eastern State Penitentiary. Therefore, the flag for this challenge is:
flag{Eastern State Penitentiary}
Bonus
JailBird
So in this bonus challenge, we’ll have to find the username of the person who has been arrested by the authorities for the crimes he has done. PD way to GOOOOOOOoo! So, let’s first look at the DEADFACE and see if we can find some articles or posts related to this incident. And Boom! I found the article. That was quick right. I know, a MAGICIAN is ME.
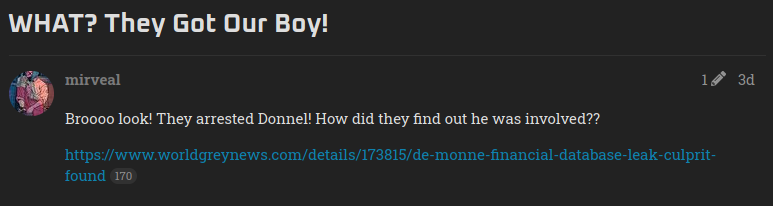
After looking at the article on the forum, I didn’t find anything interesting so I looked at the replies of the users on this post and Yay! I found the username of the Donnel who has been arrested by the authorities.
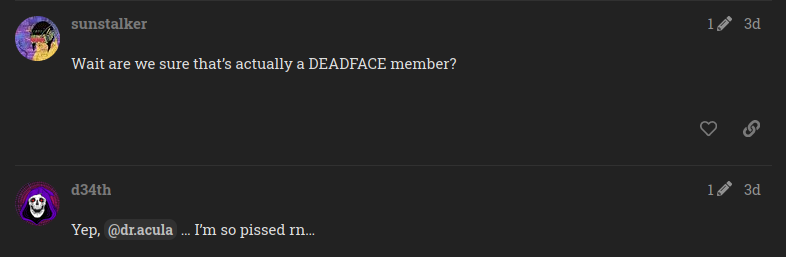
Therefore, I present the flag on behalf of Mr. Donnel(May you get out soon):
flag{dr.acula}
Traffic Analysis
Monstrum Ex Machina
In this challenge, we are provided with a Pcap Analysis File and our objective is to gather some information on the victim. So, in order to inventigate, I downloaded the pcap file and opened it in the wireshark.
So, we’ll have to find out that name of the person which the victim was searching for on the internet. So let’s take a look at the http traffic because we will find all the searches in there. Click on File and then click on Export Objects > HTTP. This will give us the list of all the http traffic.
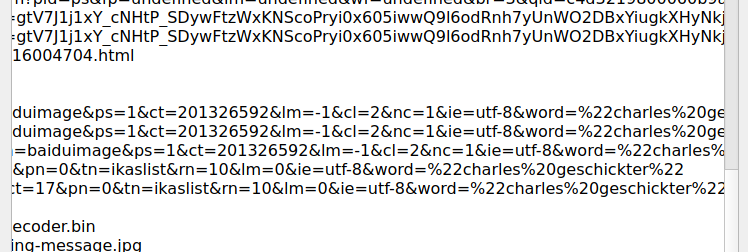
After searching through all the URLs, I found the name of the person whom the victim was searching as you can see in the above image. Therefore, the flag for this challenge is:
flag{charles geschickter}
The SUM of All FEARS
As per the challenge, we’ll have to find the MD5 sum of the two binaries which have same name but their extensions are .exe and .bin. I opened up the same PCAP file in the wireshark again and looked for the two files with same name. There is FTP data in which I found two files with the same name.
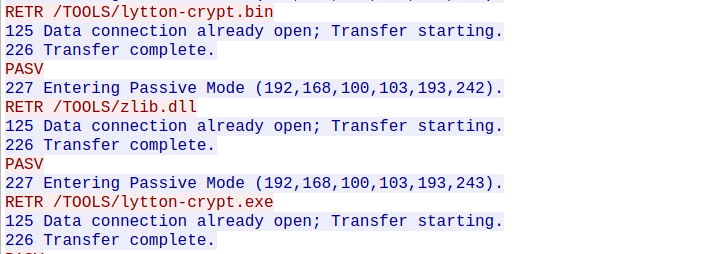
Now, we’ll have to find a way to download these two files to our machine. Luckily, whenever there is FTP data in the packet capture, there is also FTP-Data in the capture file. From that data, we can download these two files and find the MD5 sum of these files.
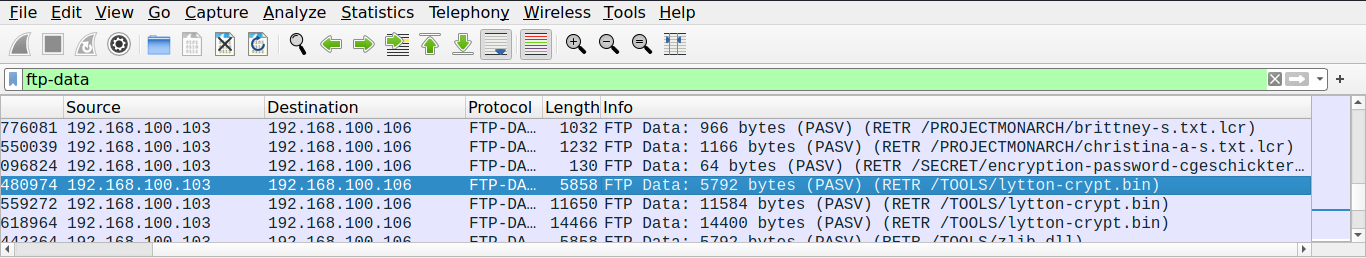
Now, follow the TCP Stream and change the choose data as to Raw format and click on the save button to save both of these files.
Now, we can find the MD5 sum of both of these files using the md5sum command. As you can see in the below image:
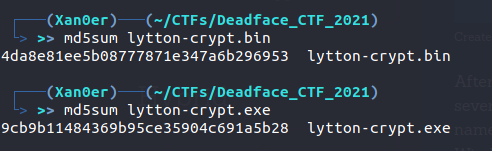
Therefore, the flag for this challenge is:
flag{9cb9b11484369b95ce35904c691a5b28 4da8e81ee5b08777871e347a6b296953}
Release the Crackin’!
In this challenge, we’ll have to find the password of the victim which was cracked by the Luciafer. Again, we’ll have to look for the password in the same pcap file. So, when I was looking through the FTP data in the pcap file, I found a password which I guess is the password cracked by the Luciafer.

Therefore, the flag for the challenge is:
flag{darkangel}
Luciafer, You Clever Little Devil!
In this challenge, we’ll have to find the packet number in which the user is granted access to the FTP.
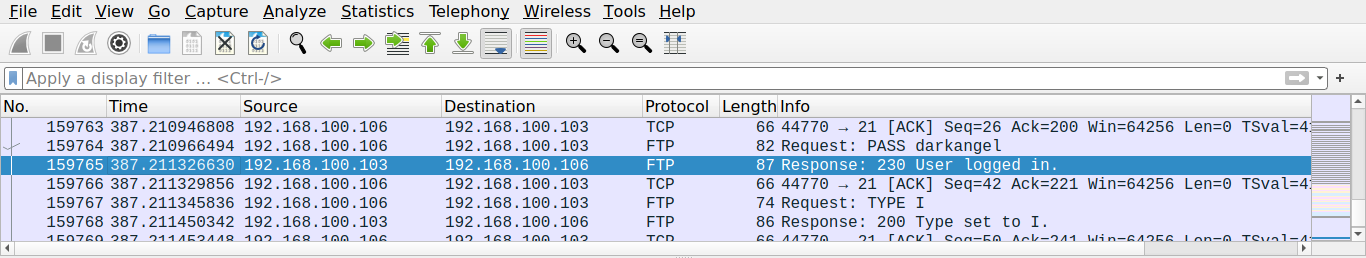
Therefore, the flag for this challenge is:
flag{159765}
A Warning
In this challenge, we’ll have to find the message which says some kind of warning. I remember that I found an image while looking through the HTTP traffic objects as you can see in the below image:
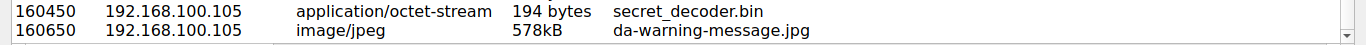
I exported the above image and stored it in my machine. Now its time to take a look at it.

Therefore, the flag for this challenge is:
flag{angels-fear-to-tread}
Forensics
Blood Bash
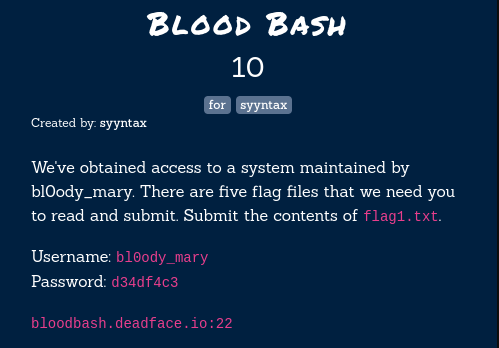
In this challenge, we’ll have to find the flag1.txt and submit the contents of that file as the flag. So first of all, we’ll have to login to the server using the given credentials via SSH. So let’s login now.
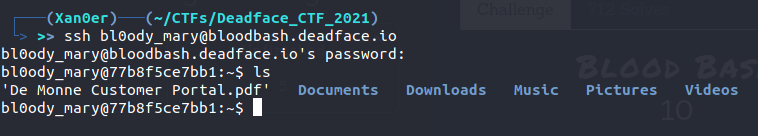
As you can see in the above image, I have loggged in to the server. Now, we have to find the flag1.txt file. So, I first of all, opened up the Documents folder and I found the flag1.txt in there.
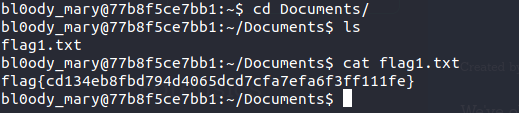
Therefore, the flag for this challenge is:
flag{cd134eb8fbd794d4065dcd7cfa7efa6f3ff111fe}
Blood Bash 2
In the challenge, again we’ll have to find the flag in the same server as the previous challenge. So, let’s go ahead and login into the server via SSH using the same credentials. So, after loggin in, I went to the same Documents folder and I found a hidden file.
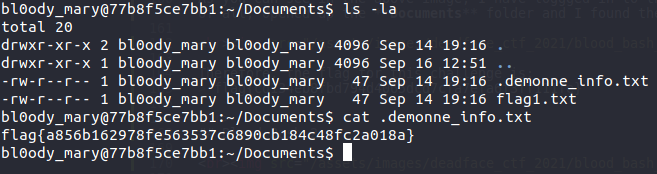
There was hidden file named .demonne_info.txt in the documents folder and when we opened up that folder, we found our flag in there. So, the flag for this challenge is:
flag{a856b162978fe563537c6890cb184c48fc2a018a}
Steganography
Send In The Clowns
In this challenge, we are provided with an image of the clowns as you can see below. So, our goal is to find the hidden flag in this image.

So, first I ran the exiftool command on the image to some details about the image but lucikly, I found the flag which was written in the comment section of the image.
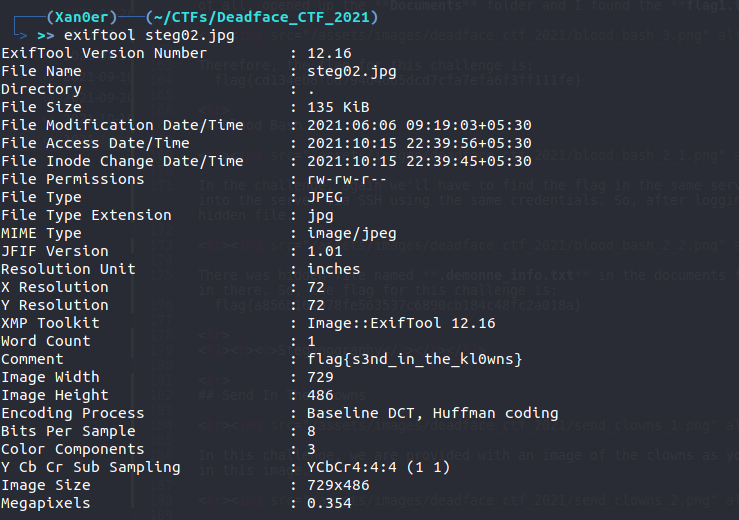
Therefore, the flag is:
flag{s3nd_in_the_kl0wns}
Scary Bunny
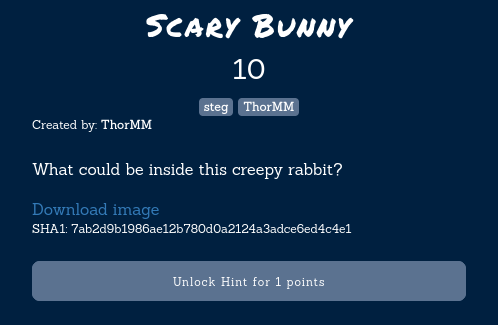
In this challenge, we are given a picture of a scary bunny and as you can see below, it really looks very scary. So, now we have to find the hidden flag in this picture.

So, I first ran the exiftool command to see what kind of information we are provided with but I didn’t saw any flag in that information. So, the next step is to try various steganography tools. So, I first tried to look for any hidden file using the steghide tool.
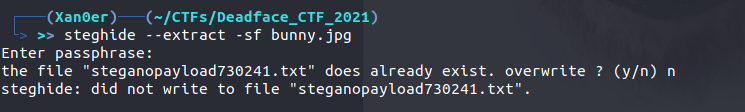
And there was a file hidden inside this image. So, when I read the content of that file, we got the flag.
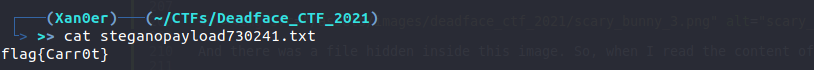
Therefore, the flag for this challenge is:
flag{Carr0t}
Behind The Curtain
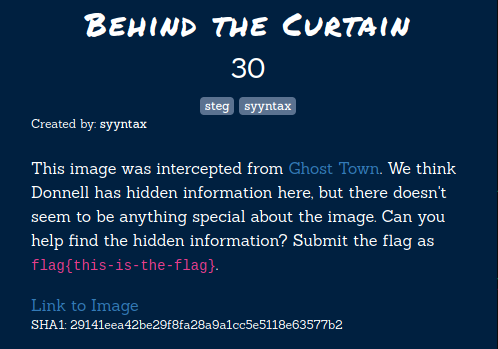
Again, in this challenge, we’ll have to find the hidden message inside the image below.

I tried various techniques to find the hidden message in this message but unfortunately, none of them worked. Then I tried to look for any hidden files in this image with the help of binwalk tool. When I ran this tool, I found out that there is a image file hiddden inside this image.
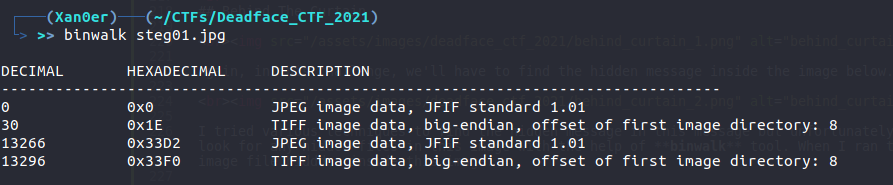
So, I extracted the file from the image using the same tool and found the flag in it.
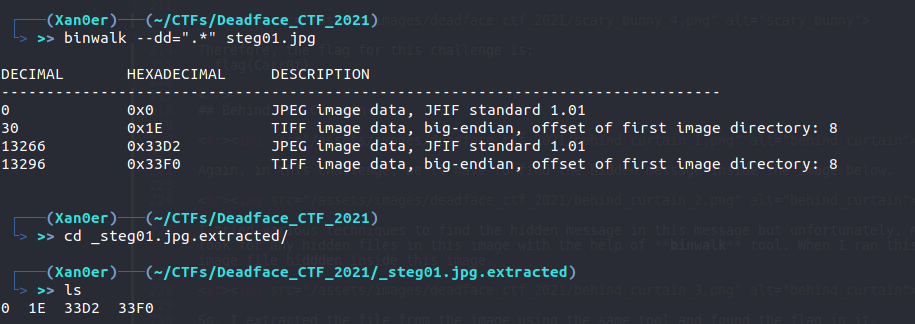

Therefore, the flag for this challenge is:
flag{L3t_m3_in}
Voice
In this challenge, we are given an audio file and we have to find the hidden flag inside this audio file. So, first, I ran the file command in order to know what kind of file this is.
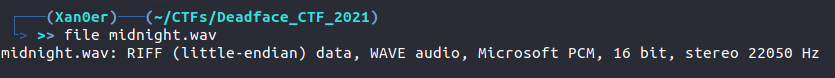
Whenever I get an audio file in a stego challenge, I run the Sonic Audio Visualizer to hunt for the hidden flags and in this case, I did the same thing. I added a layer of spectogram to the audio which gave us the flag.
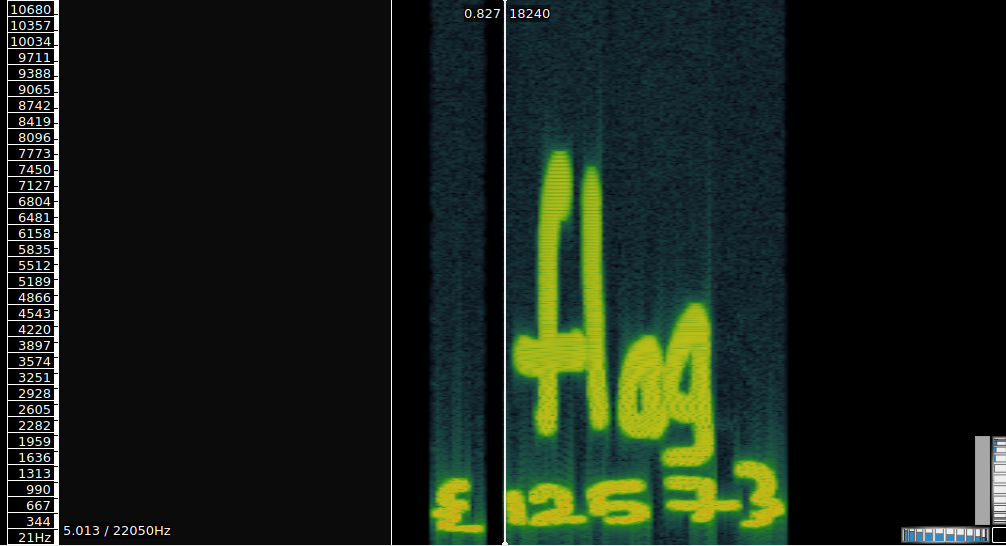
Therefore, the flag is:
flag{1257}
Cryptography
Big Boss
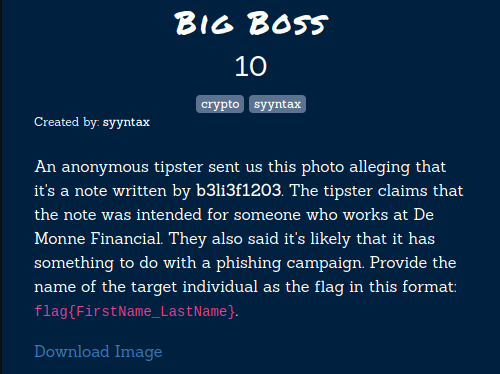
In this challenge, we are given an image in which an encrypted messsage is written. Our task is to find the first name and the last name of the target individual from this encrypted message.

I know that this a Affine Cipher since I have solved many challenges like this before. So, I go ahead and started decoding this message on dcode.fr.
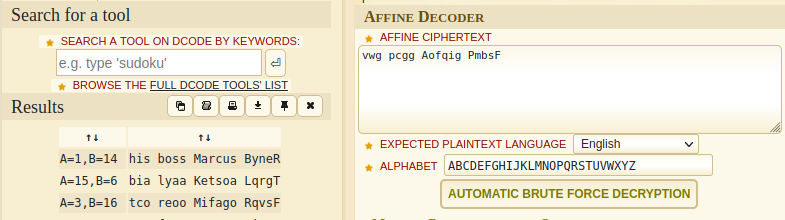
And, I found the name of the target individual. Therefore, the flag for this challenge is:
flag{Marcus_Byner}
Poor Megan
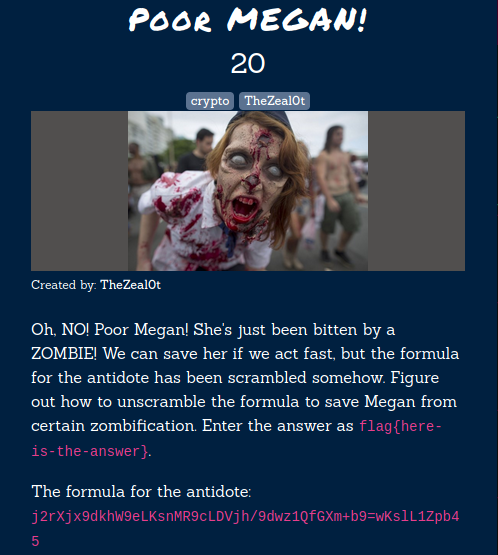
In this challenge, we’ll have to save the poor megan because she has been converted into a zombie and we’ll have to find the antidote for her. In order to find the antidote, we’ll have to decode the below cipher:
j2rXjx9dkhW9eLKsnMR9cLDVjh/9dwz1QfGXm+b9=wKslL1Zpb45
I had no idea what type of cipher this is so I went to the Cyberchef website and entered the cipher to decode it and baam! I got the receipe to make the antidote and heal the megan.
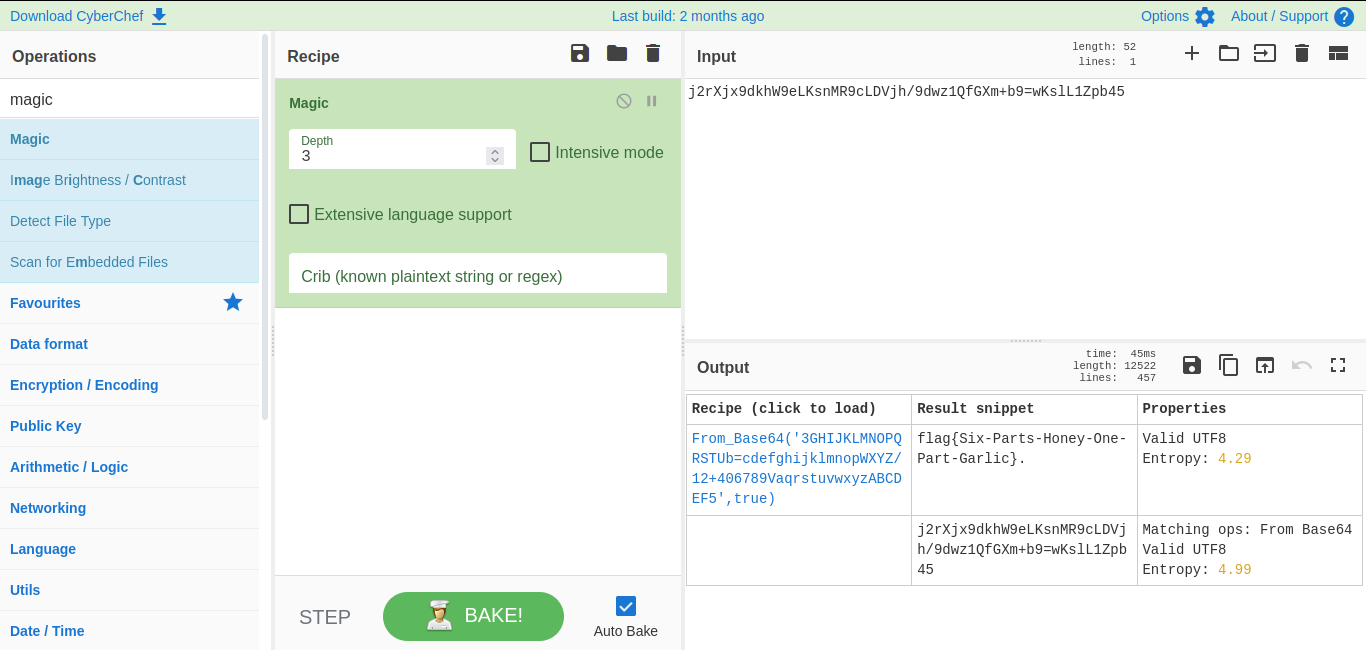
Therefore, the flag is:
flag{Six-Parts-Honey-One-Part-Garlic}
To Be Xor Not to Be
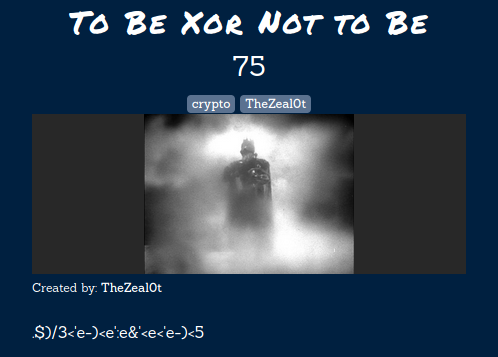
In this challenge, we are given a XOR cipher and we’ll have to decode it. This looks pretty simple.
.$)/3<'e-)<e':e&'<e<'e-)<5
I went to the dcode.fr website and opened up the XOR decoder. I entered the encrypted text and got the result as the flag that we needed.
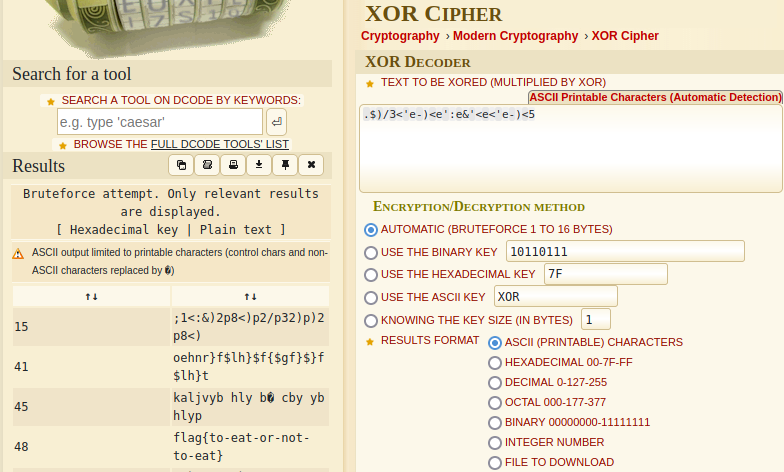
Therefore, the flag for this challenge is:
flag{to-eat-or-not-to-eat}
Exploitation
Password Insecurities
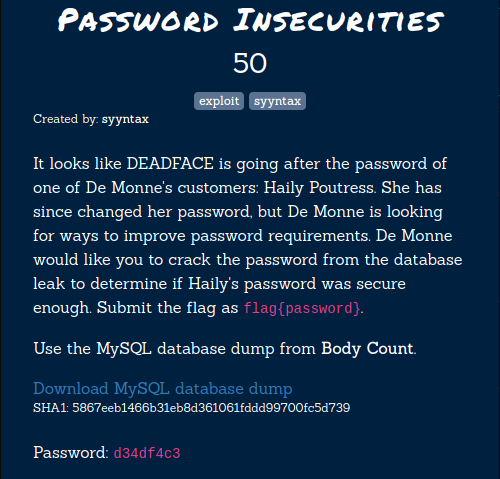
So, this challenge is based on the MySQL. We’ll have to find the password for the customer Haily Poutress and then try to crack the password. So the first step is to find the password hash. I downloaded the MySQL dump file and loaded it in the MySQL database.
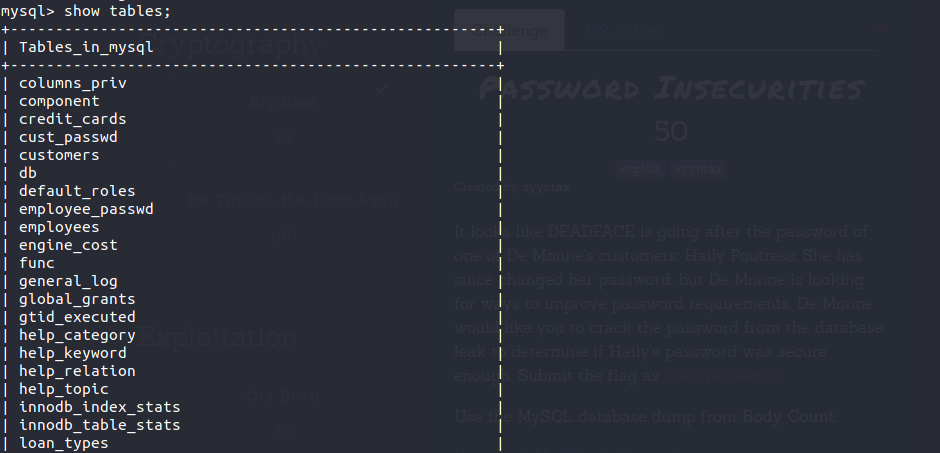
Now, we’ll have to find the password hash for the Haily. I ran the below command to find the password hash.
select * from customers where first_name = "Haily";
After I got the customer id from the above command, I ran this customer id through the password table.
select * from cust_passwd where cust_id = 7117
This gave us the password hash for the Haily user.
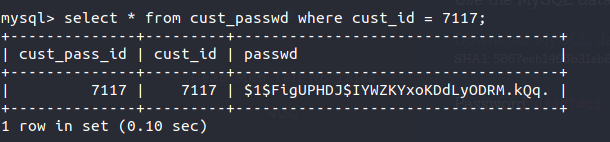
Now, we’ll have to crack this password hash. For this, I used the John The Ripper to crack this password hash.
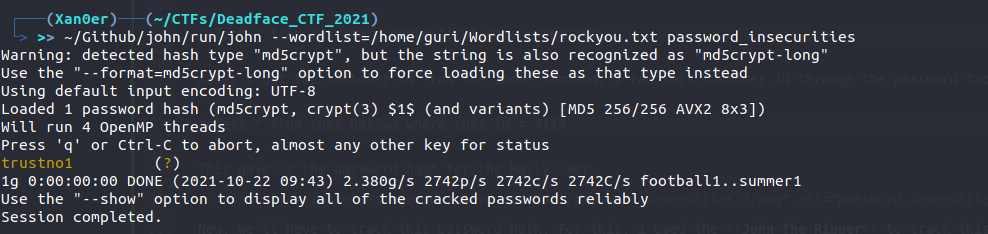
And john was successful in cracking this hash. Therefore, the flag for this challenge is:
flag{trustno1}
SQL
Body Count
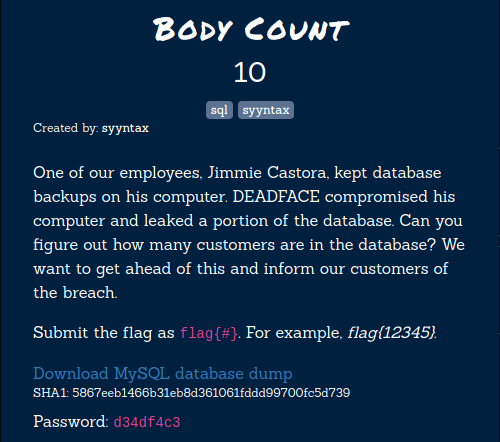
This is a challenge series in which we have to find the flags as per the challenge description. This series will test our SQL skills. I was able to solve every challenge from this category. So as per the first challenge description, we’ll have to find the total number of customers in the database. So, firstly let’s find the tables.
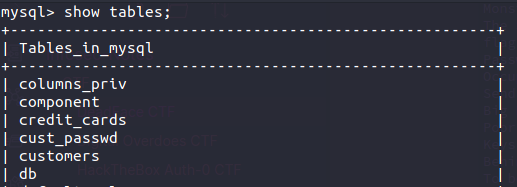
I found the customers table so now we have to find the total number of customers. For this, we will use the COUNT function of SQL.
select count(*) from customers;
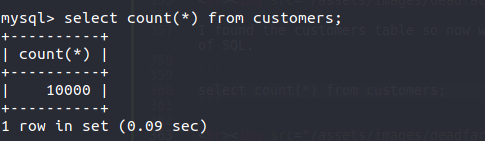
The flag is:
flag{10000}
Keys
In this challenge, we’ll have to find the any one of the foreign keys for the loans table in the database. So, I used the INFORMATION_SCHEMA function to find the foreign keys.
SELECT TABLE_SCHEMA, TABLE_NAME, COLUMN_NAME, CONSTRAINT_NAME FROM INFORMATION_SCHEMA.KEY_COLUMN_USAGE WHERE REFERENCED_TABLE_SCHEMA IS NOT NULL;
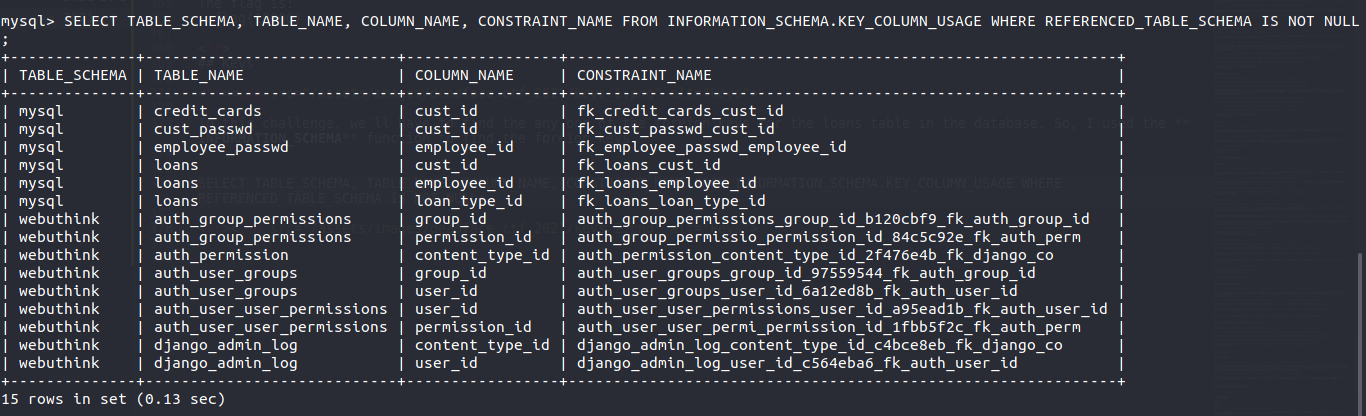
Now, we just need to pick any one of the foreign keys of loans table and submit it. The flag is:
flag{fk_loans_cust_id}
Address Book
In this challenge, we’ll have to find of customer who the DeadFace Team is targeting. As per the challenge, let’s take a look at the forum thread and see what information we can find.
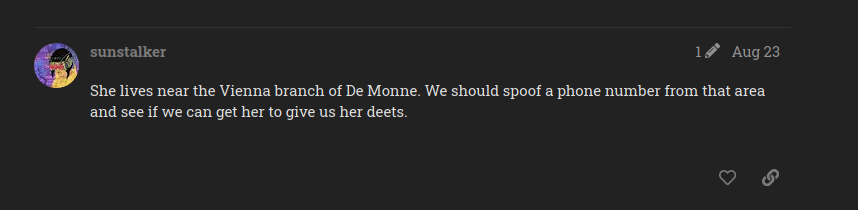
As you can see, this customer lives near the Vienna branch. So let’s try to find her in the database.
select * from customers where city = "vienna";
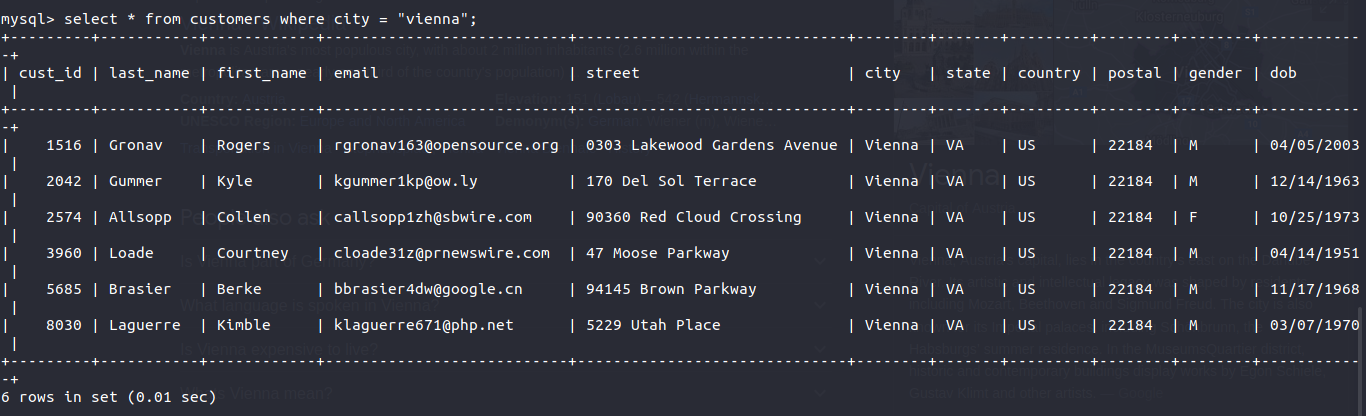
As per the information gathered from the forum, we are looking for a women who lives in Vienna and as per the above data there is only one women who lives in Vienna and her name is Collen Allsopp. The flag is:
flag{Collen Allsopp}
 Welcome to a world of CTF Learnings! Here you will find the writeups written by me on various CTF topics such as Web Exploitation, Forensics, Reversing, OSINT and much more...🐱💻
Welcome to a world of CTF Learnings! Here you will find the writeups written by me on various CTF topics such as Web Exploitation, Forensics, Reversing, OSINT and much more...🐱💻